Klotron LAB
"An Idea has got to start somewhere, and we are grateful for your thoughts!"
TODAY'S NOTES
KLOTRON PARTNER FIRST LOOK
Thank you for taking a look and sharing your thoughts and opinions. We are growing Klotron.com as a beneficial company, and we hope to have a positive impact on families worldwide through the new jobs AI can bring. We need everyone's help.
There is a form near the bottom. Please fill it out so we can send you swag and the two-ounce copper challenge coin we are planning. If you share our services with anyone, please let us know so we can track and send you coupons to use towards your next phone purchase.
LISTEN TO THE END OF THE VIDEO
Lab 101 project: Verify MC
The Domain URL for service: VerifyMC.me
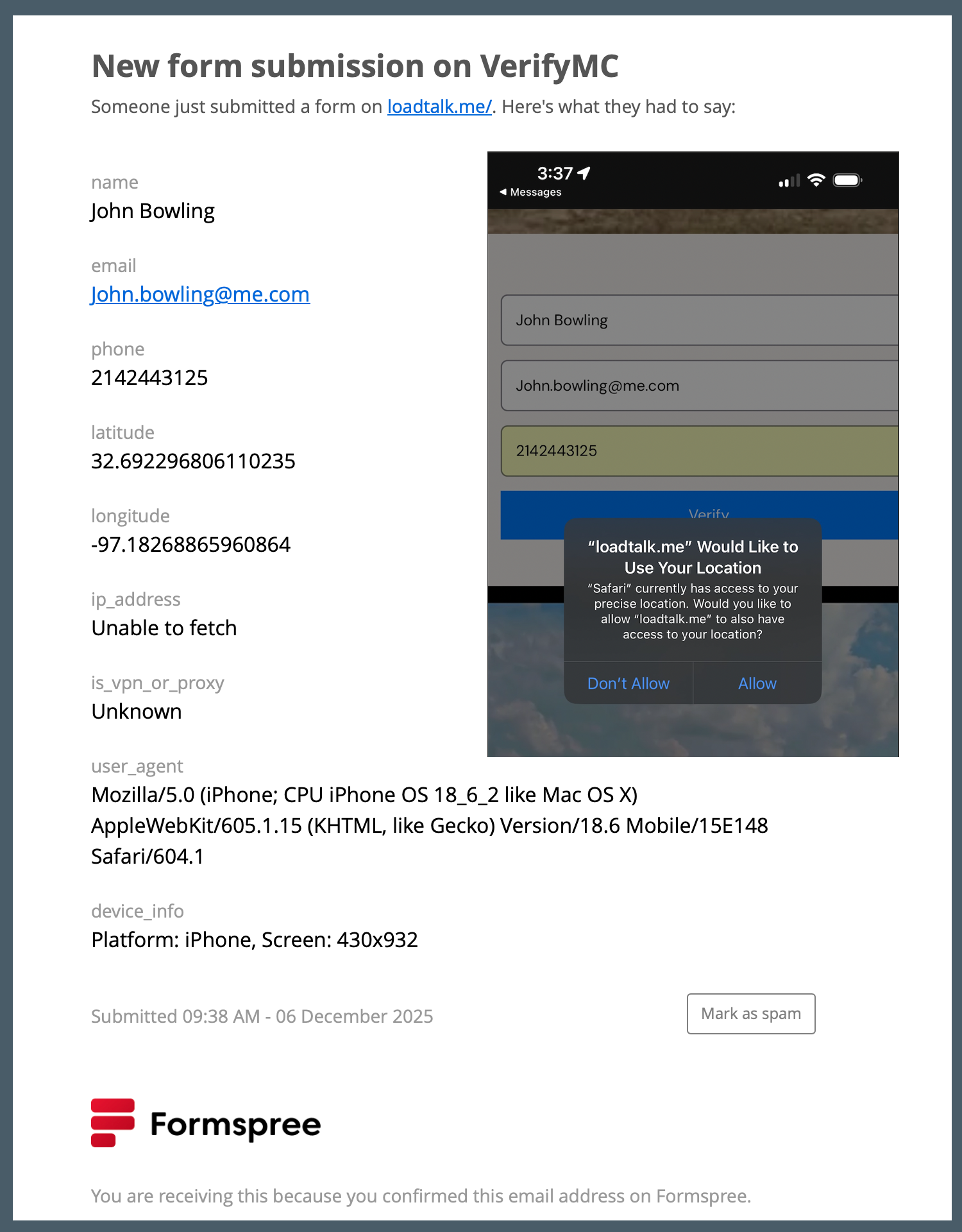
On an iPhone you should get a pop up to allow access to your location data. The is common to ask, and get when dealing with financial or sensitive data.
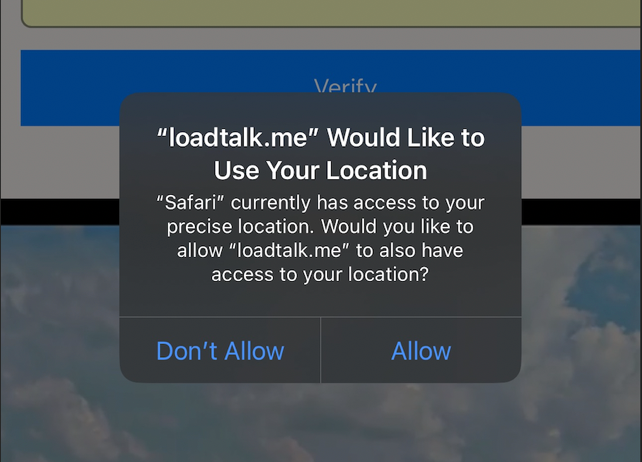
Verify MC Version 1.0.8
We need everyone with different devices to test filling out the form below. Please send any screen shots from your iPhone or Android if something different pops up and ask for permission or blocks you after you press the VERIFY button.
Add any comments to the form at the bottom
FORM NOTE: Not shown on the form is a four or five DIGIT PIN, and the legal COMPANY NAME they are doing business under. The person that is being tested enters the pin if they are using the universal page. If the client pays the annual fee they will have their own private page, and no pin is needed.
Verify MC User Physical Verification
IP and VPN Verification | Step 1: When a USER* goes to the page we will verify against a service if they are running a VPN. If they are, we will ask them to turn it off, and or step outside, turn their WiFi off and try again. We will not tell them if we gather that they are outside of the US. Customers can whitelist their IP addresses. We send the information to a Cyrus BOT**, and store the information and start building a profile if this is a new. If the user bails out on the form we keep the data and record it. Verfiy MC LLM will add it to the master record.
After Submission | Step 2: After the users fills out the form at https://verifymc.me and presses the SUBMIT button it asks their permission to grab some data. That information is gathered and the first step has taken place in the background and the information is combined in a report. For advertising, we can send a copy, real-time to the USER, and REQUESTER.
User Verify MC Report | Step 3: In step one we store the information on Cyrus, and creates a token that is included internally on step two after the USER submits the form. This data is sent to Cyrus and stored.
Requester Verification Report | Step 4: The requester, our client gets a report on the person while an API to Super Grok interrogates sources and the Internet for anything on this individual, company, e-mail, or phone number. A free service could allow people to register, get certified and freeze their information.
*USER - A user is the person with a mobile device being tested.
**Cyrus BOT (Credential Yielding Recognition Utility System) - Cyrus yields quick, reliable verification by recognizing mobile patterns, cross-referencing user IDs with location data, and utilizing smart utilities to spot inconsistencies—always with a courteous heads-up for the team.
***REQUESTER - The requester, is the client.
Fraud: Is this man and this truck real?

In truth, it's duplicated. We started with an actual stock photo and duplicated it with AI. We even created a video and can duplicate the actual trucker or owner's voice and have he or she carry on a conversation with you. Verify MC see through all that!
Carrier Identity Theft:
Cyber thieves steal the identity of a legitimate trucking company, often by obtaining their USDOT number, MC authority, and contact details from public databases or through hacking. They then impersonate the real carrier to contact brokers and book loads, passing initial vetting by providing stolen credentials. Once assigned a load, the scammers may request fuel advances, demand additional payments, or redirect the shipment to accomplices for theft, leaving the broker with financial losses and the real carrier's reputation damaged.
Double Brokering Fraud:
In this scam, perpetrators pose as a authorized carrier using fake or stolen identities to secure a freight load from a broker via load boards or direct outreach. After gaining the assignment, they switch roles to act as an unauthorized broker, reassigning the load to a legitimate but unwitting carrier at a lower rate. The scammers pocket the payment difference, often disappearing without compensating the actual hauler, or use the process to facilitate cargo theft by directing the load to fraudulent destinations.
Fuel Advance Scam:
Fraudsters, pretending to be a trucking company or driver with a valid CDL, use impersonated credentials to book a load with a broker. Shortly after, they request an advance payment for fuel or other expenses via quick-pay methods like Comchecks or wire transfers. Once the money is received, the scammers vanish without picking up the load, forcing the broker to rebook with a real carrier at additional cost while absorbing the lost advance.
Fictitious Pickup and Cargo Theft:
Scammers create phantom trucking companies with forged documents, fake websites, and spoofed phone numbers to appear legitimate and secure loads from brokers. They then dispatch impostor drivers—who may have obtained or faked a CDL—to pick up the cargo under the guise of a real haul. After loading, the thieves divert the truck to a hidden location, steal the goods, and abandon the shipment, resulting in total loss for the broker and shipper.
Account Takeover and Invoice Fraud:
Cyber criminals hack into brokers' or carriers' accounts on load boards, email systems, or payment platforms using phishing or malware. Posing as legitimate parties, they alter invoices to reroute payments to their own accounts, create fake bookings by impersonating carriers, or intercept communications to demand ransoms for "held" loads. This digital impersonation exploits trust in the supply chain, leading to diverted funds and disrupted operations.
JUST NOISE TO THINK BY!
elevator speech
I am thinking! Ideas please?
T E C H N O S P E E C H
“WE BRING DECADES OF WORK IN TRUCKING AND DECADES OF TECHNOLOGICAL EXPERIENCE"
K L O T R O N T A K E ONE
We take the what and how out of AI™
Klotron’s world-class AI-assisted services and products for the infrastructure, web, and social media help individuals and companies do more in an AI-centric world.
"In an Age of AI, a digital presence is not an option, it is a must-have."
“Today's web and social media: twelve to do”
Think of this as a Central Place to Discover and Learn AI!
E L E V A T O R S P E E C H
“Klotron simplifies AI’s complexity with powerful automation tools for the infrastructure, web, and social media that drive growth and efficiency.